
>_ TorZon Market Interface
> Verified Mirror Links
> Access Instructions
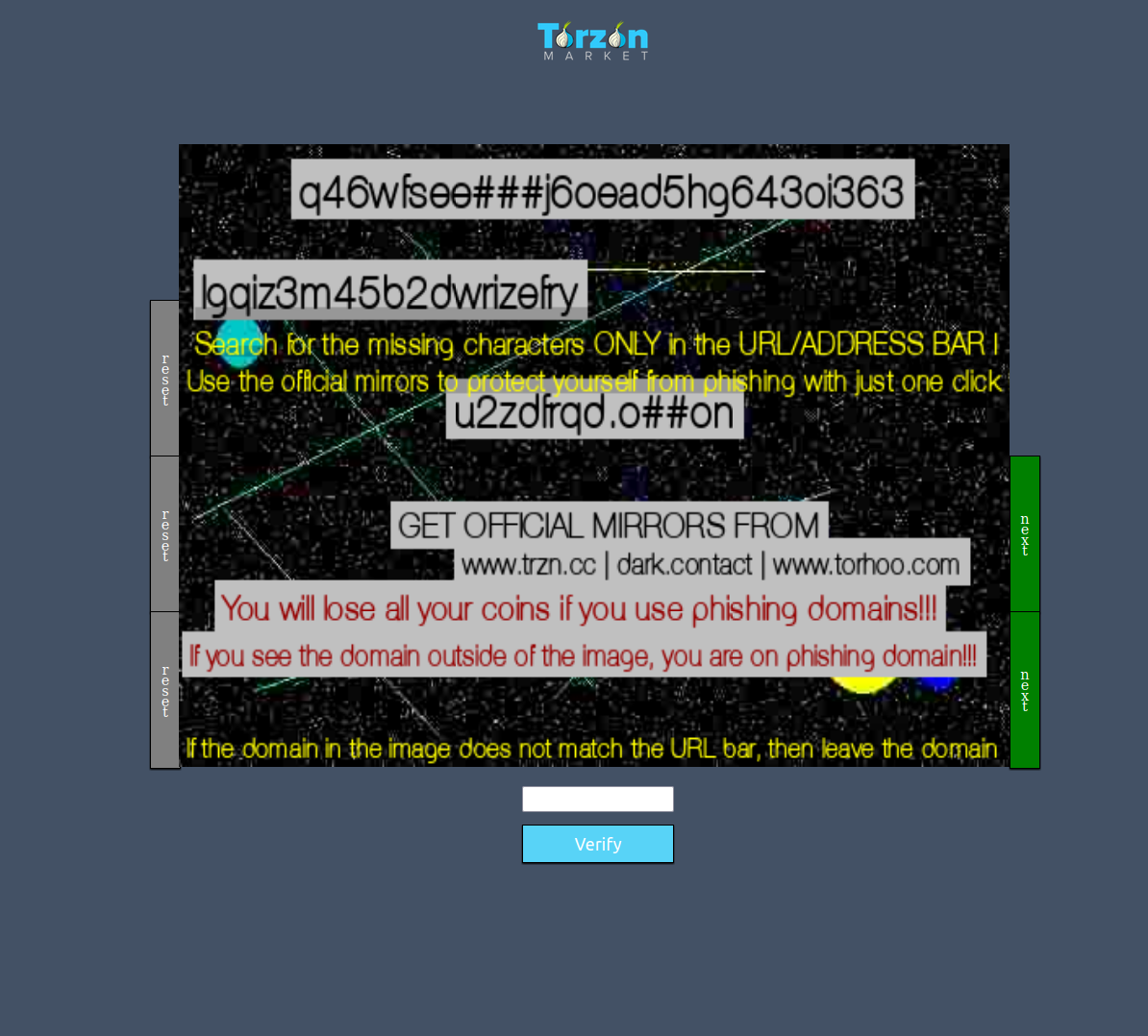
Navigating digital privacy landscapes requires more than just intent — it demands precision. To access the platform interface, users are encouraged to verify source authenticity through mirror links published via official channels. Once access is secured, a simple visual check (CAPTCHA) is followed by a minor anti-phishing challenge that ensures URL integrity. After this, visitors may proceed to register with personalized credentials, including a mnemonic backup key — a critical element in safeguarding access continuity.
> Cryptocurrencies
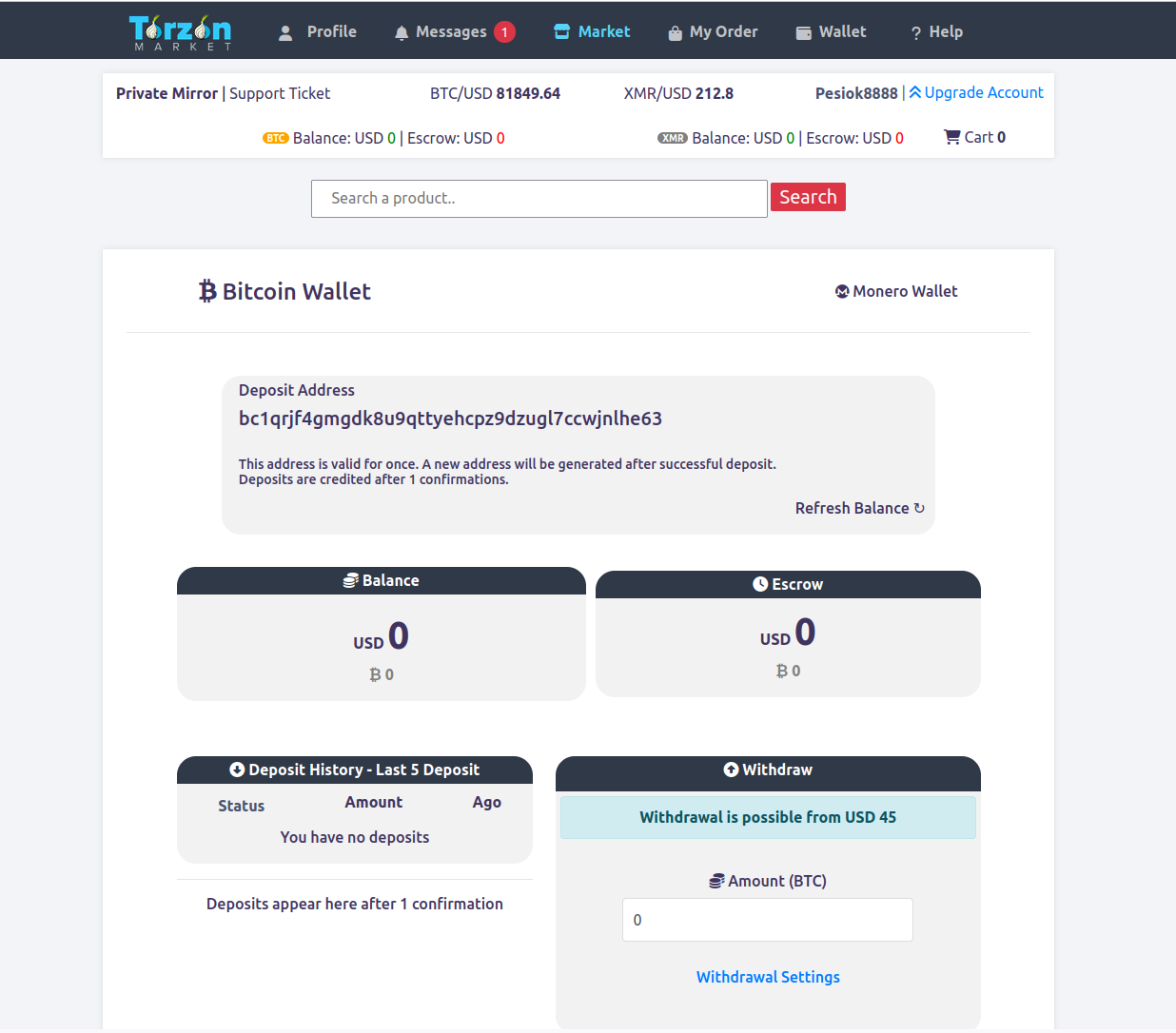
In decentralized networks, financial autonomy is key. The interface supports operations via Bitcoin (BTC) and Monero (XMR) — two of the most widely acknowledged cryptographic assets in privacy-centric environments. BTC becomes usable after 1 confirmation; XMR after 10. Each transaction generates a new receiving address, supporting layered security. Reuse of old addresses is discouraged to preserve transactional clarity.
> Security & Anti-Phishing
Data security is not optional — it’s the foundation. With Escrow-based transaction flow, optional PGP-enhanced account access, and stealth visual modes, users interact with an environment designed to reduce exposure. Phishing is actively mitigated via mirror validation, mnemonic-based account recovery, and interface segmentation — all tailored to enhance trust and operational stability.
> Authorization Flow
A properly secured entry process minimizes risk from the outset. The multi-step login structure includes visual human validation (CAPTCHA), anti-spoofing checks, and dual-factor verification. Once registered, account access is safeguarded through multiple credential layers and recoverable only via mnemonic passphrases, empowering user independence and control.



> Marketplace Preview
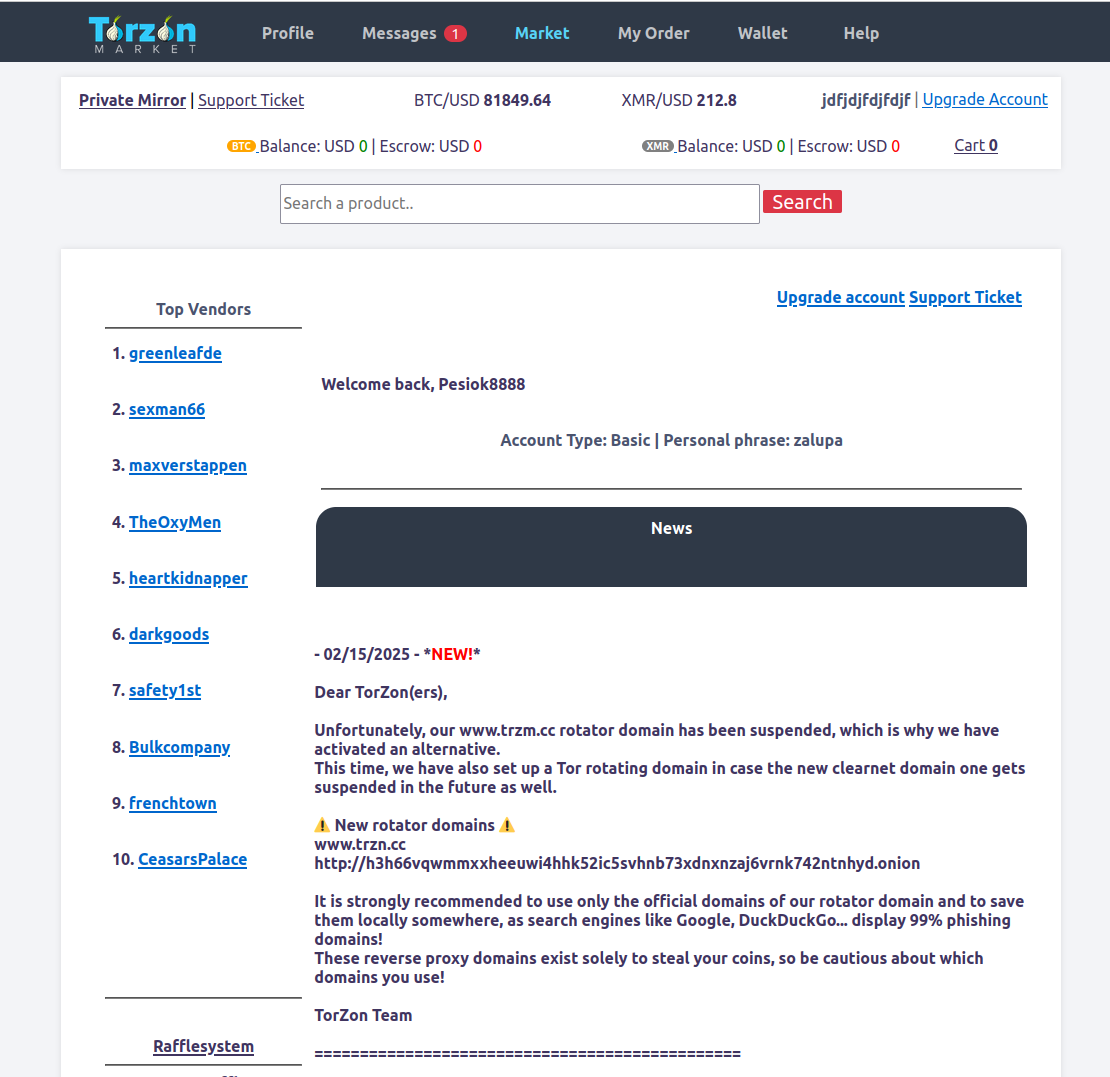
The visual layout reflects a balance between utility and anonymity. From account dashboards to financial operations, the interface is crafted to emphasize clarity while omitting unnecessary detail. Navigation is seamless, and the structure follows functional logic designed for efficiency and minimal exposure.
> Vendors & Rules
Contributors to the platform ecosystem — referred to as vendors — operate under a clear code of conduct. Verification is required to ensure authenticity, and each participant agrees to a fixed set of operational guidelines. External communications, misrepresentation, and data misuse are strictly prohibited. Visual assets must be original, and integrity is monitored.
> Raffle System & Tiers
To enhance engagement, the platform includes a dynamic ticket-based system. Participants can voluntarily join draws through individual contributions, and extended functionality is unlocked via optional account tiers. These tiers offer visual enhancements, trust feedback systems, and internal navigation benefits — strictly as a UX expansion.